Forensic investigators are presented with distinct obstacles and opportunities by Google Drive, owing to its wide usage and abundant feature set. It is a vital source of evidence since it functions as a platform for digital interactions and transactions in addition to acting as a repository for a variety of data kinds.
Understanding Google Drive
Overview
Google Drive stands as a central figure in cloud storage, offering users a platform to store, share, and collaboratively edit files. For forensic analysts, its rich set of features, such as file versioning, sharing settings, and extensive activity logs, are of particular interest. These functionalities allow investigators to track changes, access patterns, and interactions with stored data, which can be crucial in building a case.
Common Data Types Stored on Google Drive
Google Drive's versatility is evident in the variety of data it hosts, including documents, spreadsheets, images, and videos. Each file type carries specific forensic artifacts like metadata, edit histories, and sharing details, providing a wealth of information for analysis. Understanding these artifacts is key to understanding the story behind the data.
The Role of Google Drive in Personal and Professional Contexts
Google Drive's ubiquity in both personal and professional spheres underscores its importance. It's not just a storage solution but a workspace for collaboration, communication, and content management. This dual role amplifies the potential sources of evidence forensic analysts can explore, from personal projects to corporate documents, making Google Drive a focal point in digital forensic investigations.
Legal and Ethical Considerations
The legal landscape for accessing cloud storage data is complex, shaped by privacy laws such as GDPR in Europe, CCPA in California, and various other regional legislations. These laws dictate strict guidelines for data access, emphasizing user consent and legal mandates. Forensic analysts must navigate these regulations carefully, often facing jurisdictional challenges when data resides in different countries with differing laws.
Balancing the ethical considerations of user privacy with the requirements of forensic investigations is crucial. Analysts must weigh the necessity of accessing and analyzing data against the imperative to respect individual privacy rights. This balance requires a judicious approach, ensuring that investigations are both thorough and ethically sound, avoiding unnecessary intrusion into personal data unless warranted by the investigation.
Google Drive Forensics: Tips and Tricks
Google Drive Installation Articles
Before we start, for this demo we’ll be using Google Drive for Desktop which can be freely available from this link:  Google Drive
Google Drive
We will be using a Windows operating system to explore its impact on the endpoint when the application is installed.
During the installation process, Google Drive will create files and write itself into the %ProgramFiles% directory of the endpoint, as shown in the image below.

An installation log is created in the user's %APPDATA% directory. This information will become useful as we continue our discussion.

In Windows, applications including Google Drive often create registry entries upon installation. For Google Drive, relevant information can be found in the “Uninstall” registry key (HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall or HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall), detailing the application's name, installation path, and version. Additionally, Google Drive may register itself in the HKCU\Software\Microsoft\Windows\CurrentVersion\Run key to launch automatically at system startup, facilitating its sync feature without manual user intervention. However, the absence of a Google Drive entry in the Run key does not definitively indicate that Google Drive is not installed, as startup behavior is user-configurable. For a thorough investigation, check both the Uninstall and Run keys along with other indicators like Google Drive folders and files.


For the application to manage its updates it sets its configuration in the registry under HKLM\SOFTWARE\WOW6432Node\Google\Update\ClientState\<UniqueApplicationID>\
This section of the registry typically contains information about the installed state and update history of the application. The values are used by Google's update mechanisms to manage and maintain the application, ensuring that it is up to date. The presence of such a key also generally indicates that Google Drive File Stream is installed on the system and has been managed by Google's update service.
In the “LastCheckSuccess” column, you can see a value made up of numbers. These numbers can be converted to human-readable format using an epoch converter, as shown below:
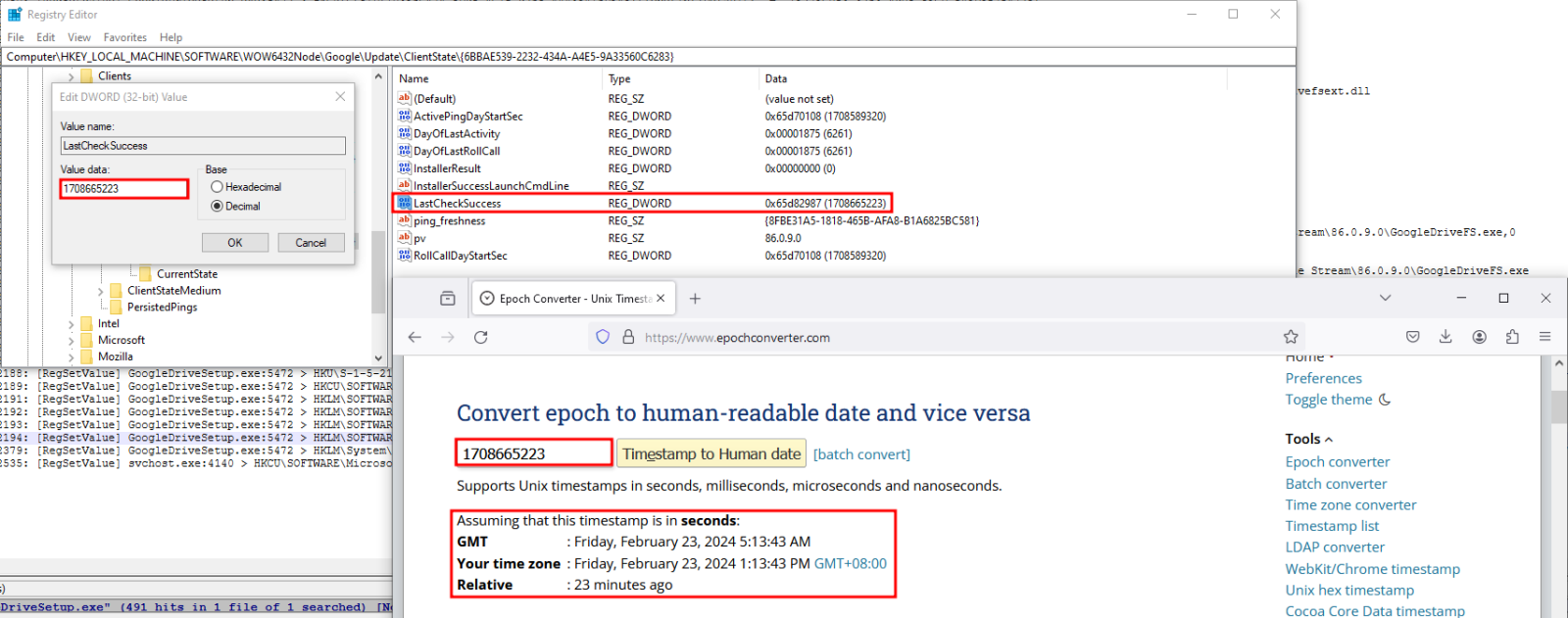
Google Drive Post-Installation Artifacts
The Google Drive application utilizes a variety of data storage methods for its configuration, which may include SQL database formats. Upon installation, it can create several database files, potentially ending in “.db”, among other storage mechanisms to ensure efficient operation and user-specific customization.

One common use of cloud storage drives is to create folders used to sync with the cloud. Google Drive stores its record of synced configured folders in HKCU\SOFTWARE\Google\DriveFS\Share registry key. In this case, our sync folder name is “TestFolder”.


Google Drive Database
For this demonstration, we will work with two separate files that we will add to and delete from Google Drive's sync folder. The files are:
- Coffee-cup-aroma.png
- Script.bat
Before beginning our analysis, let's configure Google Drive's "Mirror Files" syncing option. This setting generates a database file named “mirror_sqlite.db”, containing details about every device that has connected to the computer whilst the Google Drive app was active, as well as information on every device that has been fully or partially backed up to Google Drive.

Just to quickly recap, by default, Google Drive installs itself in two separate locations during the installation process: %ProgramFiles% and %APPDATA%. We'll begin our analysis by navigating to the %APPDATA% directory within the user's profile, where the application stores its database and other files, such as logs. The image attached below shows that these files are located in the C:\Users<user>\AppData\Local\Google\DriveFS<some_id> directory.

Let's examine some of these database files with the ".db" extension. We will use a tool called DB Browser for SQLite to inspect the “metadata_sqlite.db” file. Upon opening the file and selecting the tool's “Browse Data” option, we can view the entries for our sample files.

Recall when we enabled the “Mirror” syncing option? Google Drive also saves its file entries in a database named “mirror_sqlite.db”.

If you need to identify which directories are synchronized with the user's Google Drive, all relevant entries can be found in a database named “root_preference_sqlite.db”.

Google Drive Logs
As a forensic investigator, logs are a crucial source of valuable information. For an application like Google Drive, logs are stored in the directory C:\\Users\\<user>\\AppData\\Local\\Google\\DriveFS\\Logs. Within these logs, you can find details of all the email addresses used by the user.


Analyzing Google Drive via Memory Forensics
Forensic investigators are known to utilize the preserved volatile memory of endpoints. To conduct the investigation properly, a write blocker must be applied to prevent evidence tampering on the system. This approach minimizes the impact of our tools on the system's integrity.
In this demonstration, let's assume we have already completed the preliminary steps of the investigation, including the use of write blockers and the secure backup of disks, among other measures. Following these preparations, we then proceed to capture the memory image.

One of the initial steps in analyzing the volatile memory of an endpoint is to enumerate the processes that were active on the machine at the time of its capture. (Note: This process may take some time, depending on your resources and the size of the memory image.)
In our analysis, we observe multiple instances of Google Drive present in the memory. Our primary focus is on the first instance, which has a Process ID (PID) of 7272. All other instances are child processes of this PID. We can also see that these processes are still active on the machine because of “N/A” at the end, this is because when the process is terminated the date time will appear on that column same as “userinit.exe”.

Now that we have identified our process and the associated PID we can use volatility’s “windows.procdump” plugin to dump this process then you can use strings to dump all the readable strings that may have come with useful information.

You can also see the files that are placed in the target sync directory.

You can also use “windows.filescan” plugin to search for Google Drive’s database files.

Case Study: Adding and Deleting Files in Google's Mirror Sync Drive
As you read this section, I assume you have followed the details discussed previously. In this part, we will explore how Google Drive behaves when someone adds a file and then deletes it, particularly if the user does not want others to see the file. This is especially useful in scenarios where a user has successfully exfiltrated, downloaded, and deleted files in Google Drive.
To mimic the scenario we will delete a file named “Coffee” in our sync directory. Then, we will delete the file in the Google Drive’s trash folder.


As expected, entries in “mirror_sqlite.db” will also be updated.

But the “mirror_metadata_sqlite.db” retains the record of the files that have been placed in the target sync directory. Here’s the difference between the two databases.

Also if you look into “mirror_sqlite.db” under “deleted_items” you can see the deleted file entry.

Summary
Cloud storage has become a fundamental component of data management for organizations and individuals alike, integrating seamlessly into our digital ecosystems. For digital forensics practitioners, understanding the significance of artifacts left by cloud storage applications is crucial. These artifacts can be key to investigations, offering insights into user activities. It is also vital to utilize multiple data sources for analysis, as relying solely on one type of artifact may not provide a comprehensive view of the evidence. This multi-faceted approach ensures more accurate and reliable forensic results.
If you found this topic interesting and you don’t have any exposure to Malware Analysis, Reverse Engineering, and Incident Response, why not take a look at our Blue Team Labs Online platform.
About Security Blue Team
Security Blue Team is a leading online defensive cybersecurity training provider with over 100,000 students worldwide, and training security teams across governments, military units, law enforcement agencies, managed security providers, and many more industries.



